Building trusted customer relationships for businesses worldwide








Technology built for customers and businesses to easily transact with trust

Lightning fast and secure onboarding
Verify the identity of your customers in seconds with minimal friction to quickly convert prospects into valued customers and reach your acquisition goals.
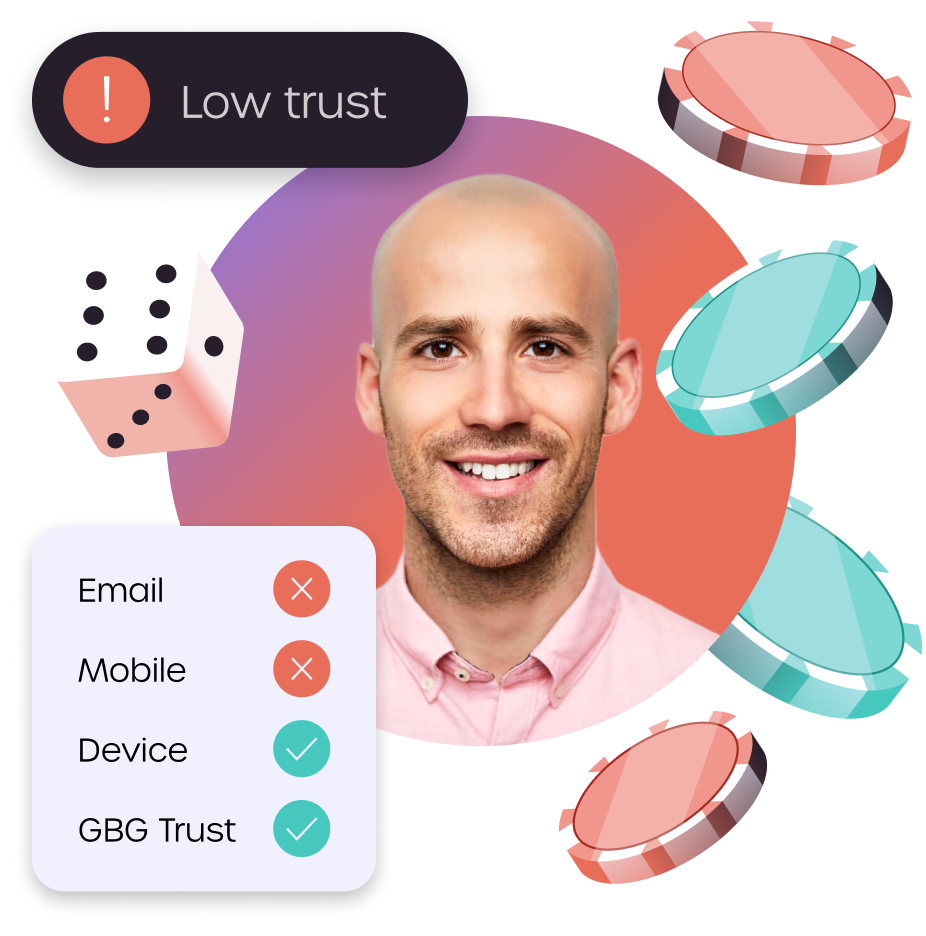
Seamless step-up authentication
Escalate to higher levels of assurance, closing the gap on hard-to-identify individuals and reducing drop-off to keep more customers in the pipeline for conversion.

Reverification without friction
Enable easy access and prevent fraud with reverification that requires minimal customer effort and provides a trusted experience.

Always on risk monitoring
Stay a step ahead of fraud and suspicious activity using predictive risk intelligence to continuously monitor transactions and identities that change over time.
Trust a proven global provider
Innovative, proven and trusted
20+ years of experience serving industry leaders with technology, data and intelligence orchestration
End-to-end solutions
Ready-made or custom workflows from front-end to back, integrate point solutions or the entire platform
One stop service provider
Everything in one place to be compliant and fight fraud with one vendor, one contract, one API
Extensive global coverage
Verify almost anyone with billions of data records, one of the industry’s largest ID libraries and biometrics
Omnichannel deployment
Cloud, on-premise, API and no code integration options to balance agility, privacy, resources and cost
Personalized support
Committed to building long-standing customer relationships through responsive service and support